Problem:
You are receiving following error while applying SSL certificate to you SAP Web application server:
CA certificate missing in database (or is not unique) Message no. TRUST057.
Cannot import certificate response.
Steps to Troubleshoot:
- Verify your certificate request.
You can do this by using any of the CA’s websites. For example Symantec below:
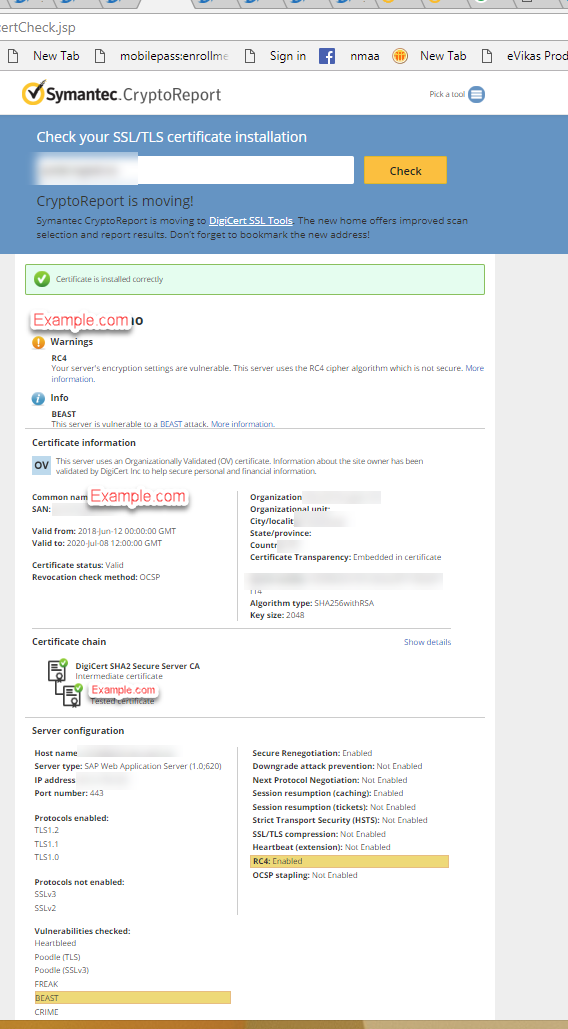
https://cryptoreport.websecurity.symantec.com/checker/views/csrCheck.jsp
Generate Request from SAP (STRUSTSSO2):

Paste the CSR into the checker:
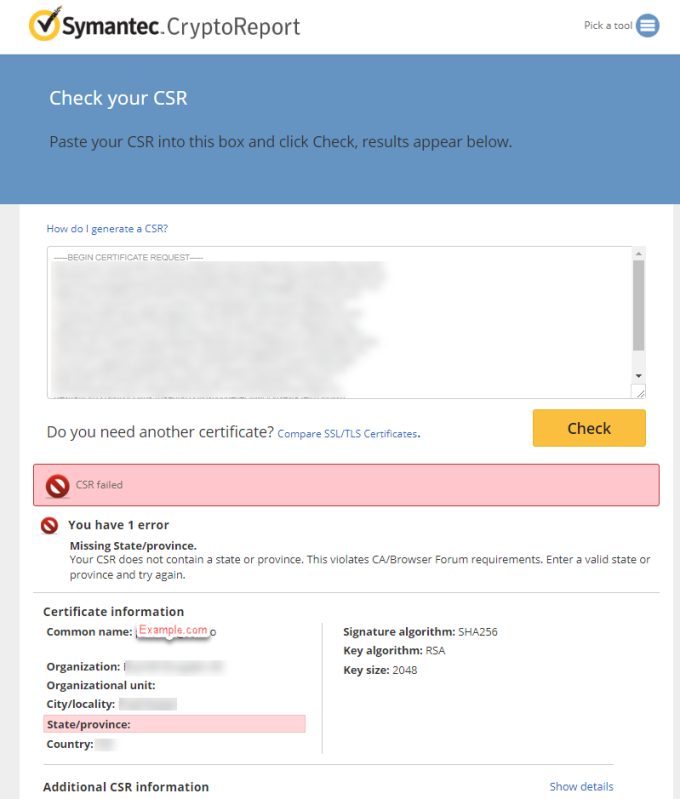
Main thing to check here is the Common Name. This should exactly correspond to the portal url being used by the end users.
In this example certificate will only work if used with portal example.com. It will not work if it is http://www.example.com or media.example.com.
If you are getting any other Common Name then the required one, delete the Server PSE and create new one with correct CN.
Make sure that SSL Server’s own certificate contains CN as the portal name you connect to and the hostname (Unless both are same).
User following guidelines:
- Country Name (C): Use the two-letter code without punctuation for country, for example: US or CA.
- State or Province (S): Spell out the state completely; do not abbreviate the state or province name, for example: California
- Locality or City (L): The Locality field is the city or town name
- Organization (O): If your company or department has an &, @, or any other symbol using the shift key in its name, you must spell out the symbol or omit it to enroll.
- Organizational Unit (OU): This field is the name of the department or organization unit making the request.
- Common Name (CN): The Common Name is the Host + Domain Name. It looks like “www.example.com” or “example.com”
- Get the right certificate chain
Most of the times, Signed certificates sent by CA will not include the complete chain, i.e. root and intermediate certificates.
These are generic certificates and are not specific to your application.
You can check this by opening the certificate using a notepad.
If you dont have the root and intermediate certificate, you can directly download these from CA’s website.
For example, Symantec certificates can be downloaded with below url:
https://knowledge.digicert.com/generalinformation/INFO4033.html#links
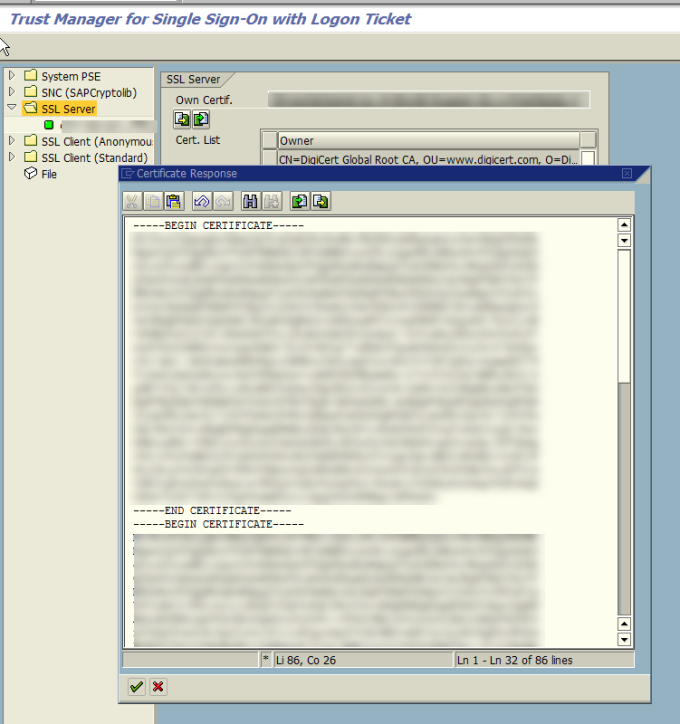
- Import the certificate into SAP
Now combine all three certificates into one file in any order and save it as a .CER file.

Import certificate into SAP. You can either use the file created or just copy paste into the window.
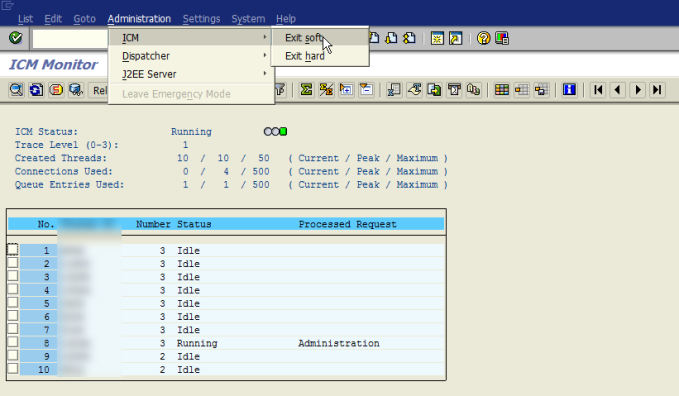
- Restart ICM
For these changes to take effect, you must restart your ICM.
- verify the certificate:
The HTTPS connection can now be verified by using vendor portal or third-party checkers. Symantec is used below:
https://cryptoreport.websecurity.symantec.com/checker/views/certCheck.jsp