Procedure to refresh your expired SAP Router certificate with new one. I have included some screenshots for better understanding.
Check the validity of your router using below command:
sapgenpse get_my_name
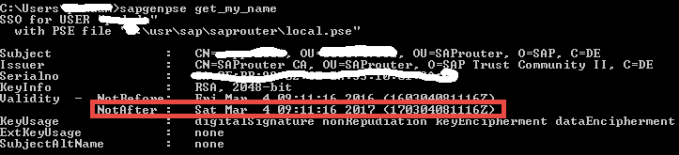
Usually the validity of certificate is only for one year.
A. Login to SAP Market Place to get the distinguished name of your router server:
https://support.sap.com/remote-support/saprouter/saprouter-certificates.html
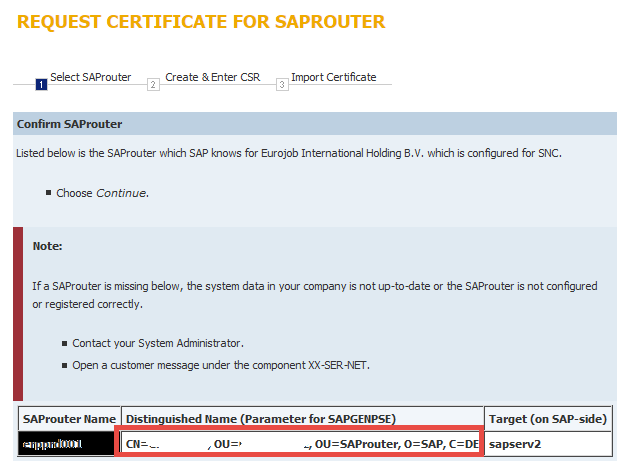
Before executing the next steps, make sure that you have taken the backup of complete SAPROUTER folder (Or which ever directory containing your SAP Router). Delete the following files local.pse, srcert, certreq and cred_v2 from SAPROUTER folder.
B. Generate the certificate Request with the command:
sapgenpse get_pse -v -r certreq -p local.pse “<Distinguished Name>”
Example:
sapgenpse get_pse -v -r “E:\usr\sap\saprouter\certreq” -p local.pse “CN=myserver, OU=0000123456, O=saprouter, O=SAP, C=DE”
Got absolute PSE path “E:\usr\sap\saprouter\local.pse”.
Please enter PSE PIN/Passphrase: ****
Please reenter PSE PIN/Passphrase: ****
!!! WARNING: For security reasons it is recommended to use a PIN/passphrase
!!! WARNING: which is at least 8 characters long and contains characters in
!!! WARNING: upper and lower case, numbers and non-alphanumeric symbols.
Supplied distinguished name: “CN=Myserver, OU=0000123456, OU=SAProuter, O=SAP, C=DE”
Creating PSE with format v2 (default)
succeeded.
certificate creation… ok
PSE update… ok
PKRoot… ok
Generating certificate request… ok.
Certificate Request
Signed Part
Subject :CN=Myserver, OU=0000123456, OU=SAProuter, O=SAP, C=DE”
Key
Key type :rsaEncryption
Key size :2048
Attributes
Signature
Signature algorithm :sha256WithRsaEncryption
Signature (size=”2048″) :<Not displayed>
You will be asked to enter the pin twice. Do make a note of the pin as you will be using it later.
C. Create SAP Router Certificate:
On SAP Marketpace, select the certificate you want to generate the request for and continue:

Copy and paste the content of file “certreq” on the next screen (From begin to end and no space included)
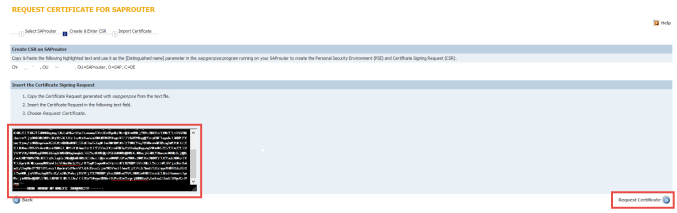
Now your SAP Router certificate is ready. Copy the certificate from “Begin certificate” to “End Certificate” and paste the content to file named “srcert”, which must be created in the same directory as the sapgenpse executable.
D. Install the SAP router certificate
Install the certificate using the below command,
sapgenpse import_own_cert -c srcert -p local.pse
example output:
Please enter PIN:
CA-Response successfully imported into PSE “D:\usr\sap\saprouter\local.pse”
E. Create credentials for SAP router
Execute below command to generate credentials for SAP Router.
sapgenpse seclogin -p local.pse -O <user_for _saprouter>
Example output:
running seclogin with USER=”routadm”
Please enter PIN:
Added SSO-credentials (#0) for PSE “E:\usr\sap\saprouter\local.pse”
“CN=myserver, OU=0000123456, OU=SAProuter, O=SAP, C=DE”
Note: The account of the saprouter user should always be entered in full <domainname>\<username>. If you do not enter a user here, credentials will be generated for currently logged in user.
This will create a file called “cred_v2” in the same directory as “local.pse”
F. Check the certificate.
Execute below command to check the new validity of the certificate:
sapgenpse get_my_name -v -n Issuer
The name of the Issuer should be:
CN=SAProuter CA, OU=SAProuter, O=SAP, C=DE
And below command to check the validity:
sapgenpse get_my_name
Sample output:
SSO for USER “routadm”
with PSE file “E:\usr\sap\saprouter\local.pse”
Subject : CN=myserver, OU=000012345, OU=SAProuter, O=SAP, C=DE
Issuer : CN=SAProuter CA, OU=SAProuter, O=SAP Trust Community II, C=DE
Serialno:
KeyInfo : RSA, 2048-bit
Validity – NotBefore: Fri Mar 010 17:22:45 2017
NotAfter: Thu Mar 08 17:22:45 2018
