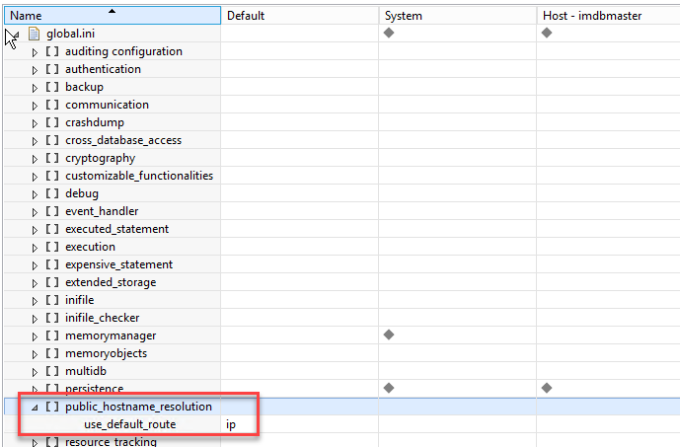
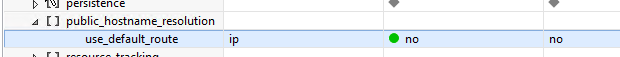
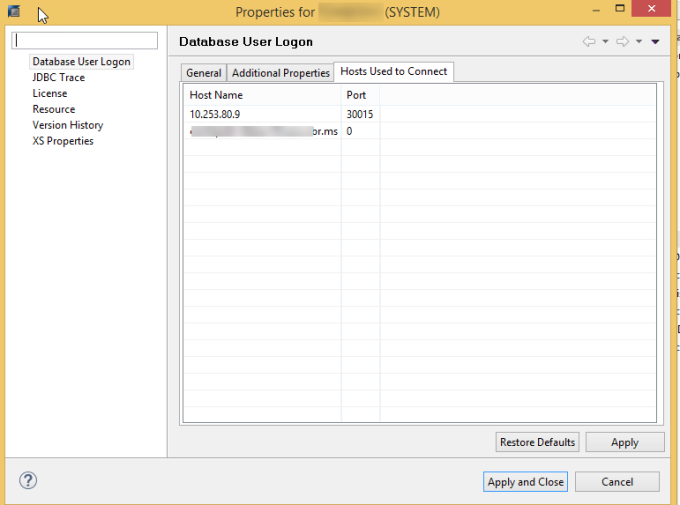
As continution to the previous blog Prepare SAP HANA for SSL, I am writing this blog to use SSL with SAP HANA Studio.
Even if do not want to use SSL with studio, this procedure can be used at leset to test SSL that has been configured on the SAP HANA server.
- Copy the root and server certificates (PEM) created during configuration of SSL to the client machine (Where Studio is installed).
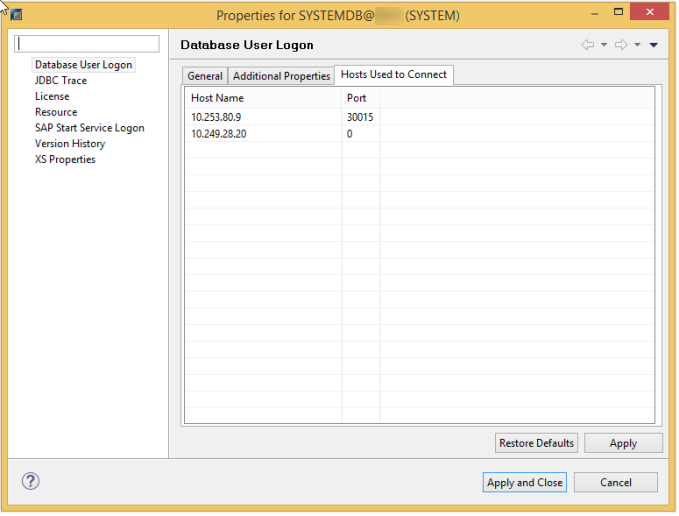
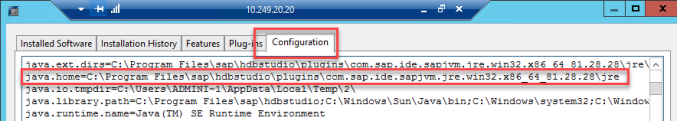
- Check the java keystore path from studio properties:
- Create Keystore and import required Root Certificate
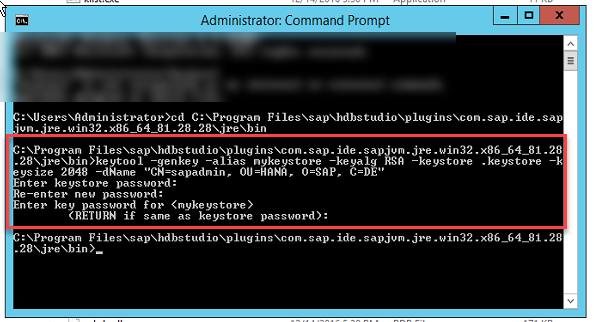
Open command prompt and naviagate to $java.home/bin.Execute command:keytool -genkey -alias mykeystore -keyalg RSA -keystore .keystore -keysize 2048 -dName “CN=Firstname Lastname, OU=HANA, O=SAP, C=DE”
- Import the Root Certificate to the .keystore container.
Note: You cannot use certificates in P7b format.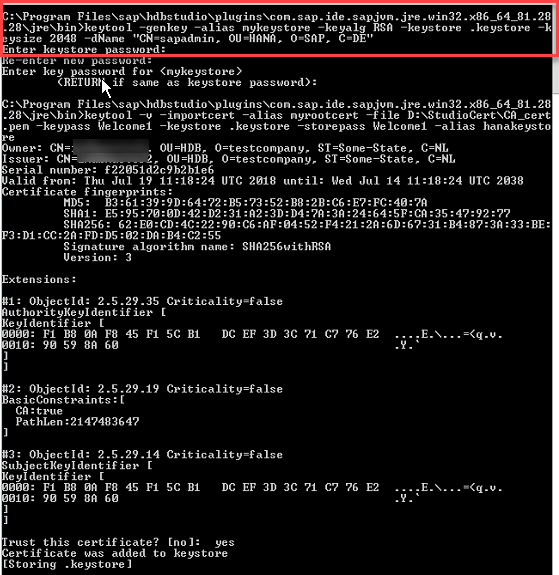
You are now ready to connect to SAP HANA server via HANA studio using SSL.
Test:
I am attaching additinal steps/screenshots from the errors so that it will be easy for others to troubleshoot similar issues:
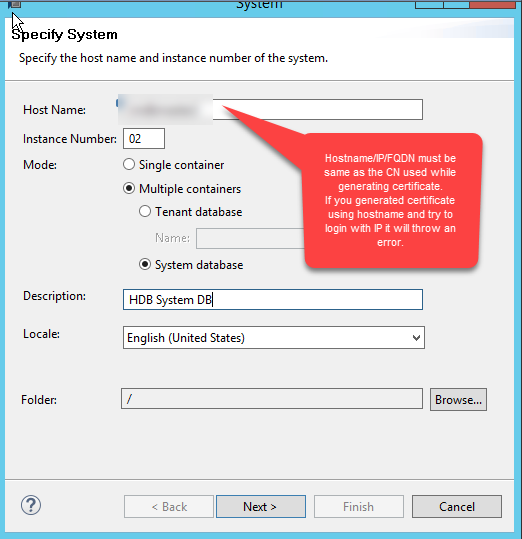
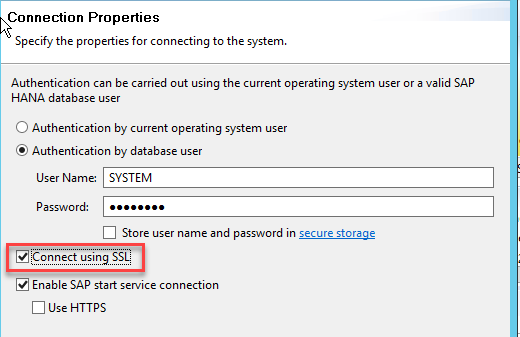
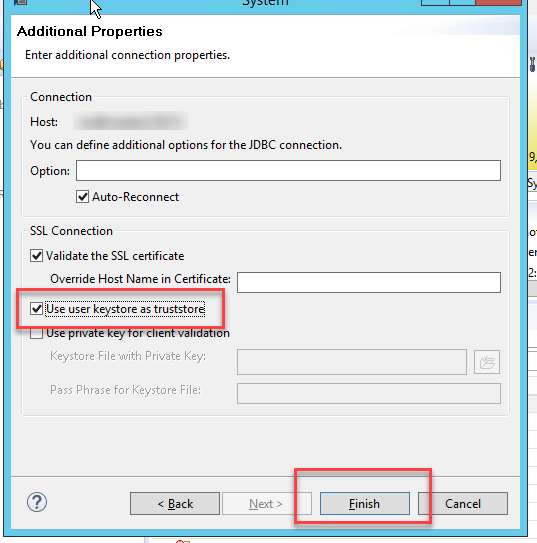
Once added you will see a small lock on the system indicating that the connection is going via SSL.
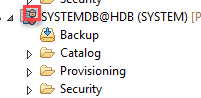
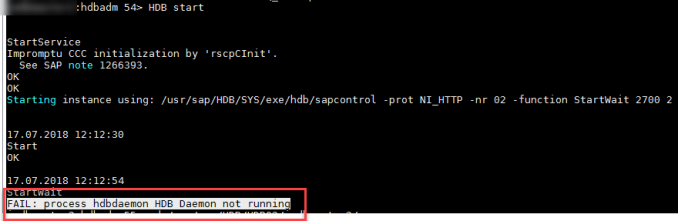
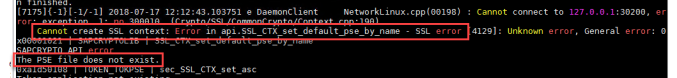
Troubleshooting:
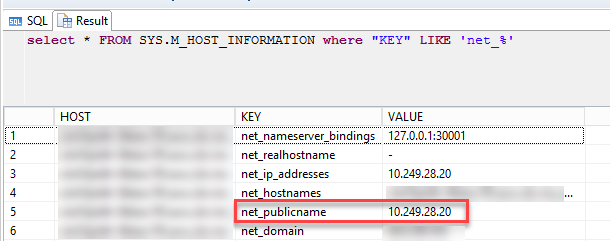
Errors can be check with log from studio as below:
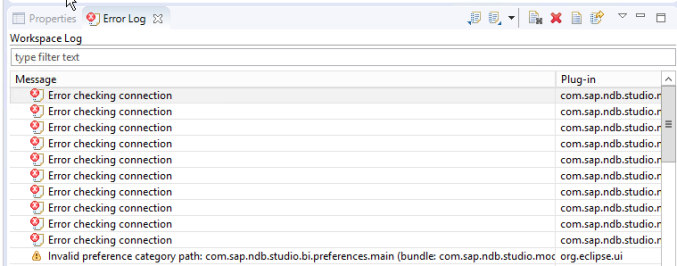
You can open each error to get more details.



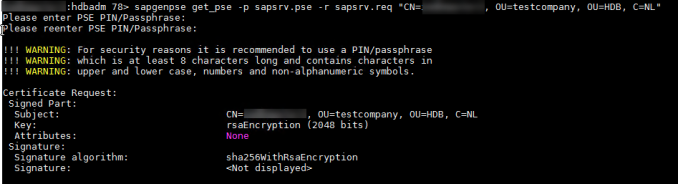 Important Note:
Important Note:

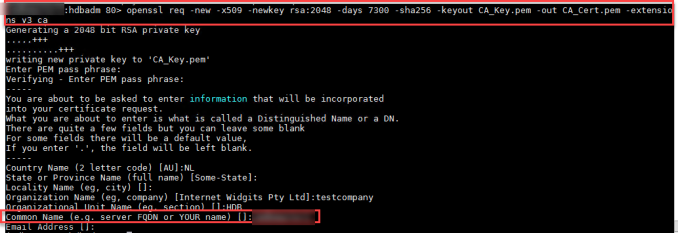 Here you can use the pass phrase that you want.
Here you can use the pass phrase that you want.

 With this step you have the certificate ready that can be used on Client machines.
With this step you have the certificate ready that can be used on Client machines. Note that the pse file has a new timestamp with certificate added.
Note that the pse file has a new timestamp with certificate added.